This week, Let’s Encrypt announced the launch of multi-perspective validation, an effort that helps address a fundamental flaw baked in to the way websites are verified and encrypted. The deployment of multi-perspective validation will help reduce the ability of network-level adversaries to exploit a high-level vulnerability that makes it possible for Internet traffic to be intercepted en masse. Evidence suggests this exploit has been actively employed by repressive governments (see research on BGP hijacking campaigns targeting Iranian users of Telegram and Instagram, Pakistan Telecom hijacking YouTube traffic, or China Telecom misdirecting Internet traffic between multiple countries, for example).
Specifically, the existing weakness pertains to the domain validation process, through which website operators are able to prove that they actually control the domain in question. Server administrators apply to a certificate authority (CA), such as Let’s Encrypt, to obtain a certificate. This can be accomplished through use of Electronic Frontier Foundation (EFF)’s free and open source Certbot tool (also an OTF-supported project) which automates the process of obtaining an HTTPS certificate.
Together, CAs act as trusted third parties in what’s known as the Public Key Infrastructure (PKI) system. If successfully validated, this digitally signed certificate usually ends up displayed to users on their Internet browser via a small padlock icon near the address bar. The problem with domain validation is that, “ironically, the mechanism that CAs use to issue certificates is itself vulnerable to man-in-the-middle attacks by network-level adversaries,” as noted by the research team at Princeton University in their work (pdf) demonstrating the real-life applicability of such an attack. Princeton’s OTF-supported research focused on how Internet traffic can be hijacked by exploiting vulnerabilities in the Border Gateway Protocol (BGP), which is used to exchange routing information at the network-level.
As Let’s Encrypt says, “if a network attacker can hijack or redirect network traffic along the validation path (for the challenge request, or associated DNS queries), then the attacker can trick a CA into incorrectly issuing a certificate.” While Let’s Encrypt notes that “such attacks are rare,” Princeton’s research showed, in a controlled environment, how it works.
In their blog post, Let’s Encrypt explains how multi-perspective domain validation will help mitigate such attacks:
“…The Border Gateway Protocol (BGP) and most deployments of it are not secure. While there are ongoing efforts to secure BGP, such as RPKI and BGPsec, it may be a long time until BGP hijacking is a thing of the past. We don’t want to wait until we can depend on BGP being secure, so we’ve worked with the research team from Princeton to devise a way to make such attacks more difficult. Instead of validating from one network perspective, we now validate from multiple perspectives as well as from our own data centers:
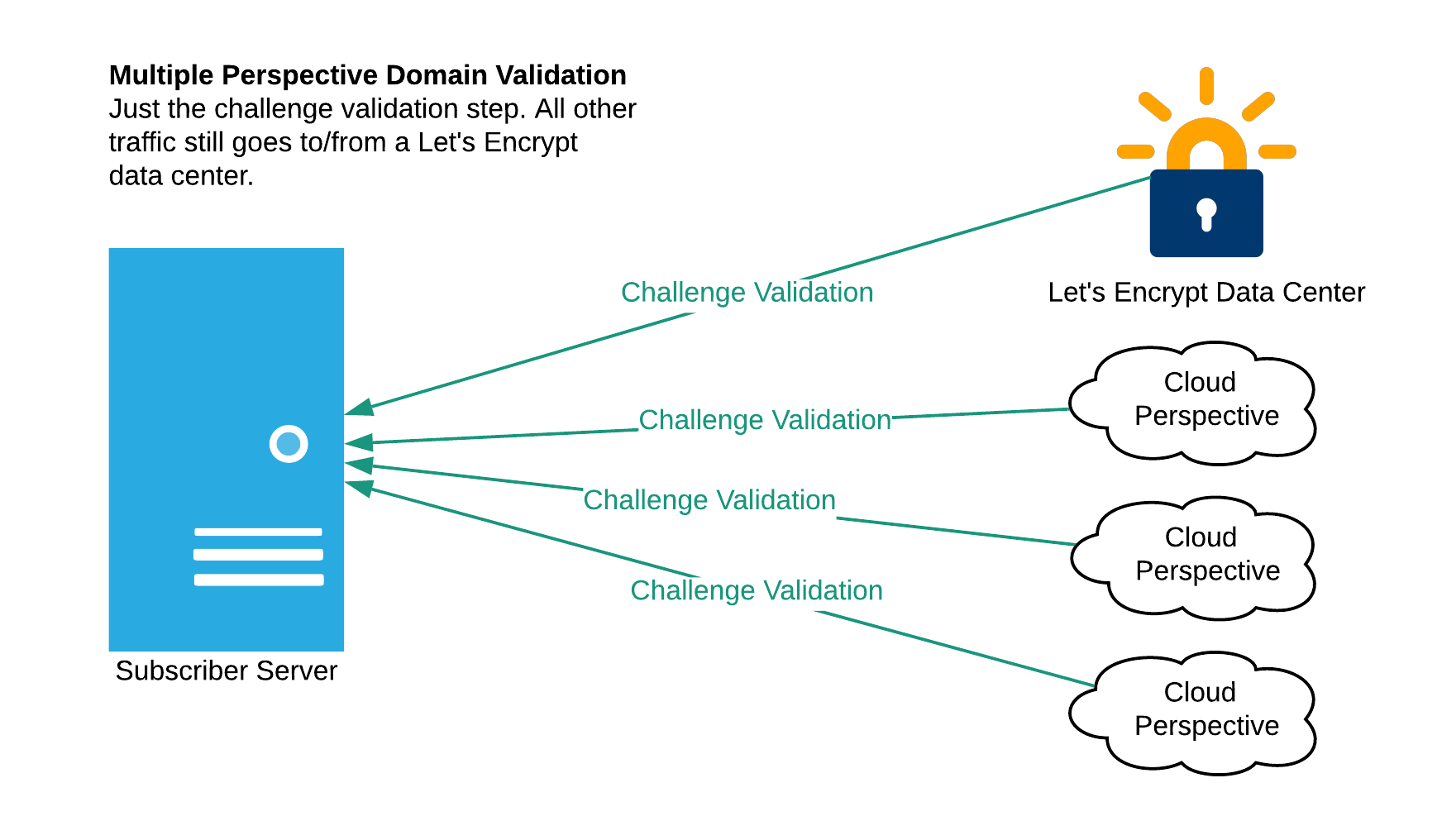
Image via Let’s Encrypt
Today we are validating from multiple regions within a single cloud provider. We plan to diversify network perspectives to other cloud providers in the future.
This makes the kind of attack described earlier more difficult because an attacker must successfully compromise three different network paths at the same time (the primary path from our data center, and at least two of the three remote paths). It also increases the likelihood that such an attack will be detected by the Internet topology community.”
Read the full Let’s Encrypt blog post here: Multi-Perspective Validation Improves Domain Validation Security.

